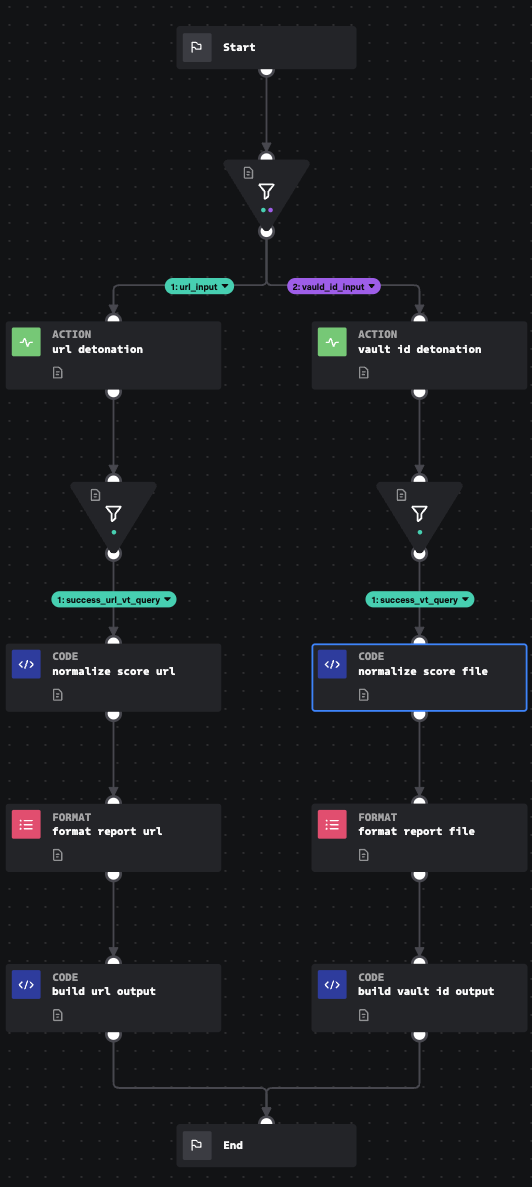
VirusTotal V3 Dynamic Analysis
Description
Accepts a url link, domain or vault_id (hash) to be detonated using Virustotal V3 connector.
- Type: Investigation
- Product: Splunk SOAR
- Apps: VirusTotal v3
- Last Updated: 2023-03-23
- Author: Teoderick Contreras, Splunk
- ID: 388ed434-a498-4d55-8de4-b2657825cb67
- Use-cases:
- Enrichment
- Phishing
- Endpoint
Associated Detections
How To Implement
This input playbook requires the Virustotal V3 API connector to be configured. It is designed to work in conjunction with the Dynamic Attribute Lookup playbook or other playbooks in the same style.
D3FEND
| ID | Technique | Definition | Category |
|---|---|---|---|
| D3-DA | Dynamic Analysis | Executing or opening a file in a synthetic "sandbox" environment to determine if the file is a malicious program or if the file exploits another program such as a document reader. | File Analysis |
Explore Playbook
Required field
Reference
source | version: 1