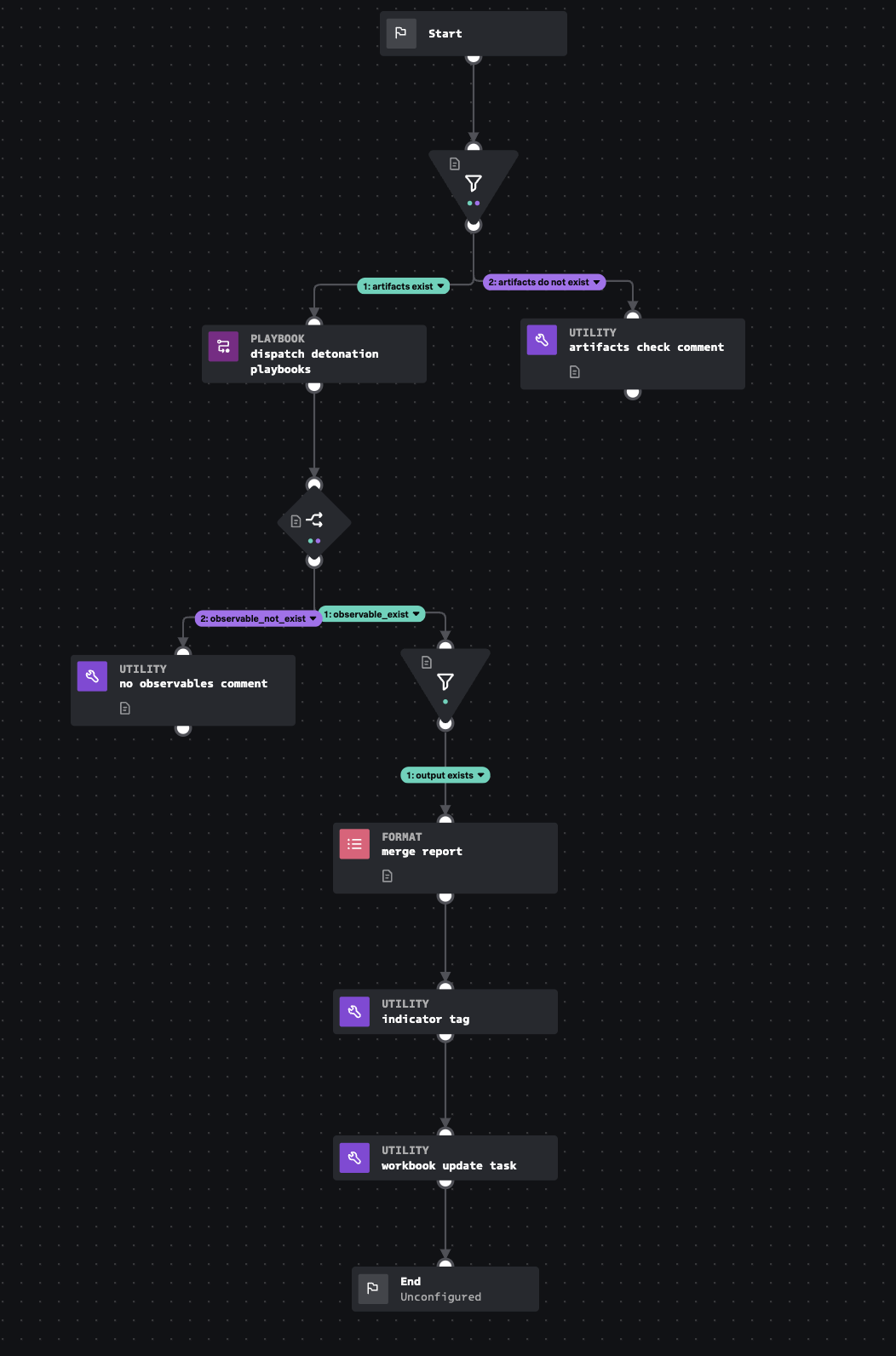
Dynamic Analysis Dispatch
Description
Automatically dispatches input playbooks with the 'sandbox' tag. This will produce a merge report and indicator tag for each inputs.
- Type: Investigation
- Product: Splunk SOAR
- Apps:
- Last Updated: 2023-03-30
- Author: Teoderick Contreras, Splunk
- ID: a15da934-1f59-4672-b98c-ec1bbfd80885
- Use-cases:
- Enrichment
- Phishing
- Endpoint
Associated Detections
How To Implement
This automatic playbook requires "sandbox" tag be present on each input playbook you want to launch.
D3FEND
| ID | Technique | Definition | Category |
|---|---|---|---|
| D3-DA | Dynamic Analysis | Executing or opening a file in a synthetic "sandbox" environment to determine if the file is a malicious program or if the file exploits another program such as a document reader. | File Analysis |
Explore Playbook
Required field
Reference
source | version: 1