AWS Find Inactive Users
Description
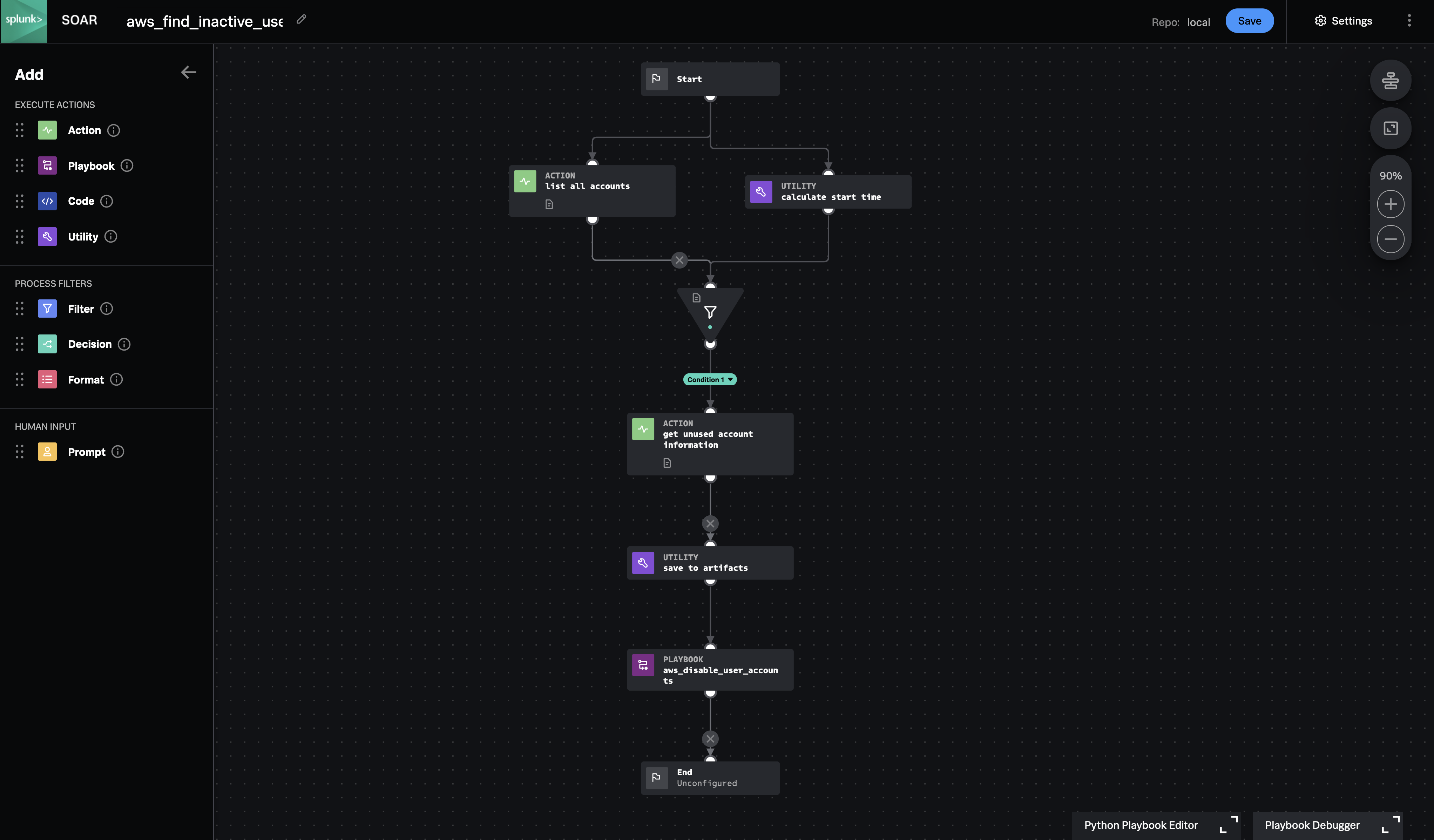
Find AWS accounts that have not been used for a long time (90 days by default). For each unused account, gather additional group and policy information and create an artifact to enable further automation or manual action.
- Type: Investigation
- Product: Splunk SOAR
- Apps: AWS IAM, Phantom
- Last Updated: 2021-11-01
- Author: Philip Royer, Splunk
- ID: fc0edc76-ff2b-48b0-5f6f-63da6423fd63
- Use-cases:
Associated Detections
How To Implement
This playbook is meant to run on a Timer, such as once per week. To adjust the lookback period away from the default, change the number of days to a different negative number in the 'calculate_start_time' block. Note that this playbook will ignore accounts where the password has never been used. These could be unused human accounts or they could be API accounts where the access keys are actively used.
Explore Playbook
Required field
Reference
source | version: 1