Active Directory Reset password
Description
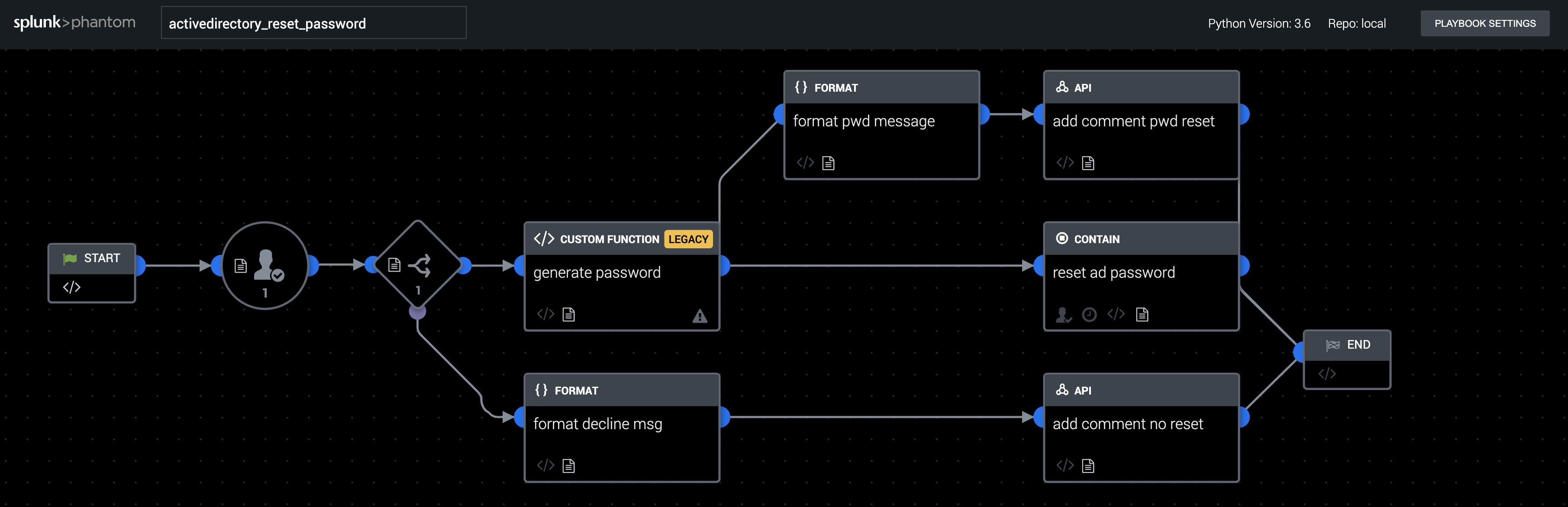
This playbook resets the password of a potentially compromised user account. First, an analyst is prompted to evaluate the situation and choose whether to reset the account. If they approve, a strong password is generated and the password is reset.
- Type: Response
- Product: Splunk SOAR
- Apps: AD LDAP
- Last Updated: 2020-12-08
- Author: Philip Royer, Splunk
- ID: fc0edc96-ff2b-48b0-9f6f-63da6783fd63
- Use-cases:
Associated Detections
How To Implement
This playbook works on artifacts with artifact:*.cef.compromisedUserName which can be created as shown in the playbook "recorded_future_handle_leaked_credentials" - The prompt is hard-coded to use "admin" as the user, so change it to the correct user or role
Explore Playbook
Required field
- compromisedUserName
Reference
source | version: 1