AWS IAM Account Locking
Description
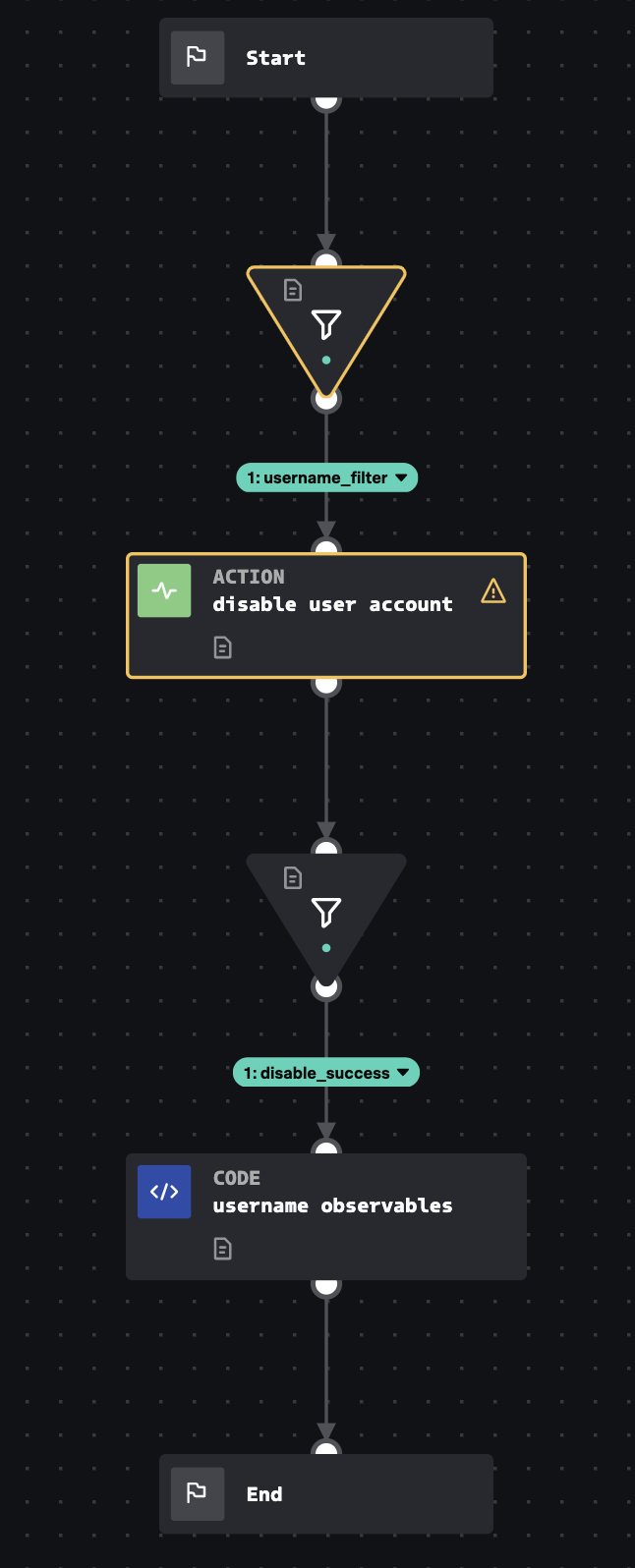
Accepts user name that needs to be disabled in AWS IAM Active Directory. Disabling an account involves deleting their login profile which will clear the user's password. Generates an observable output based on the status of account locking or disabling.
- Type: Investigation
- Product: Splunk SOAR
- Apps: AWS IAM
- Last Updated: 2023-05-08
- Author: Teoderick Contreras, Splunk
- ID: f15e4ab7-b057-4225-86ae-c36ab78b50f2
- Use-cases:
- Phishing
- Endpoint
Associated Detections
How To Implement
This input playbook requires the AWS IAM connector to be configured. It is designed to work in conjunction with the Dynamic Attribute Lookup playbook or other playbooks in the same style.
D3FEND
| ID | Technique | Definition | Category |
|---|---|---|---|
| D3-AL | Account Locking | The process of temporarily disabling user accounts on a system or domain. | Credential Eviction |
Explore Playbook
Required field
Reference
source | version: 1